The previously announced June 25 attack on North Korean websites by hackers working under the “Anonymous” name took an unexpected turn on Tuesday when several South Korean sites were hit with attacks. The actions coincided with the release of what hackers said were stolen files on American military personnel.
The North Korean attack did start as scheduled and appears to have been initially successful. Most major North Korean websites are either inaccessible or difficult to access, indicating they are being hit by a denial of service attack. This involves overwhelming a web server with requests so it gets tied up and bonafide traffic doesn’t get through.
The Anonymous hackers had chosen June 25 because it’s the anniversary of the start of the Korean War. The plans had been announced a couple of months in advance and North Korea’s state-run news agency, KCNA, even ran a commentary over the weekend attacking their plans and rubbishing the group.
North Korean military documents
As part of the build-up to Tuesday’s attack, Anonymous said it had gained access to North Korea’s internal intranet system and stolen documents. The claim was met with skepticism and Anonymous said it would make a partial release of documents on Tuesday.
As of time of writing, that has not happened.
Confusion at start of attack
Perhaps a sign of the chaotic nature of the Anonymous hacker collective came shortly after the attacks got underway at midnight local time in Korea. One of the first targets turned out to be one of the most vocal Anonymous members on Twitter.
His own site was hit with a denial of service attack.
A follow up message indicated it had been the result of a mix-up, and a fellow Anonymous hacker had misunderstood the nature of the site.
Blue House Attack
For part of the day, the website of the South Korean president’s office, the Blue House, was defaced.
A YouTube user posting under the name “Bondra James” in a freshly created account uploaded a 2-minute video that appears to show the attack on the Blue House website taking place. A large “Anonymous” watermark covers part of the screen.
The computer being used in the video is named “AnonAR” and the user is employing a toolkit called “w3b_avtix.”
The toolkit apparently contains software to gain access to websites because within about 20 seconds of running the software, the attacker appears to be inside the South Korean president’s website. [Update: The video has been removed from YouTube as a violation of its policy on depiction of harmful activities.]

A message advising to come back later greets visitors to the Blue House website after a hacking attempt.
Wider Attacks
Other reports said attacks had hit the sites of broadcasters KBS and YTN, although they appear to have been recovered.
The attacks even reached outside of the Korean peninsula. Although the reason is unclear, OpNorthKorea hackers attacked a government website for Zibo City, a provincial city in Shandong, China.
A website from Zibo City in China’s Shandong province is shown after being attacked by hackers on June 25, 2013.
US Military Lists
Coinciding with the attacks, several files containing personal data were uploaded to text-sharing websites, which allows users to post text messages anonymously.
Several files contained what appear to be the personnel records of members of the U.S. Army’s 3rd Marine Division, 25th Infantry Division and 1st Cavalry Division. The records contain a name, date of birth, rank, social security number and other information related to their service.
Together, the records appear to detail some 7,500 persons, but none of the dates on any of the records in the three files is later than 2009, so the lists could be old.
Also posted were a list of hundreds of names and birthdates claimed to be of Korean military members, user names and login details for accounts on the Blue House website and names, cell phone numbers and more for members of the ruling Saenuri party.
The veracity of all of the information could not be immediately confirmed.
(more to come)



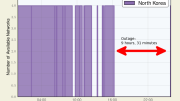

While I don’t dispute the attacks have been successful, Anonymous have claimed many more sites to be “completely offline” when they aren’t. I’m not sure how thorough they are with their checks but my data is often different from theirs.
I use several thousand proxy servers to trawl kcna.kp for updates to database 24/7, interestingly kcna.kp is not behaving very differently from the past weeks access logs. It seems to be standing up better than a lot of others.
Update:
From the selected NK sites I monitored, chosonsinbo.com was “down” for a period of two hours, uriminzokkiri and ryugyongclip were also taken out.
kcna.kp was “totally unresponsive” for less than 0.1% of the 24 period we have been monitoring it, which is within the margin of error. Other sites have responded more strongly.
This information is available at the live monitoring page http://kcnawatch.nknews.org/sandbox/kp.status.php?site=no-head-foot