Karaoke is a uniting past time for North and South Korea, with noraebang commonly available throughout Pyongyang, and Video CDs long a ubiquitous commodity. It comes as little surprise then, that karaoke machines have made their way to Pyongyang.
In this post, I take a look at the Tianchi v700, a Chinese karaoke machine that has been localized for the North Korean market. The hardware was listed online at the end of 2018, and purchased from a seller in Dandong, China in February, 2020.
From a quick look at the menu, it’s obvious that some effort has been spent crafting this media experience for a North Korean audience. The Tianchi v700 is a reasonable data point of the experience once could expect at a KTV room in Pyongyang.

The Tianchi v700 (Photo: Will Scott)
A window into a different world
The Tianchi v700 blurs the distinction between devices meant for Chinese and Korean audiences much more than android phones and tablets, which are also manufactured by Chinese OEMs for a Korean audience. The device is meant to be used in a commercial KTV setting, where it would be hooked up to a large TV, speaker system, and microphone input. It features a large 19″ touch screen, running a kiosk version of Android, and comes in discrete, unbranded packaging with a range of both Chinese and North Korean karaoke songs preloaded.

The Tianchi v700 (Photo: Will Scott)
The North Korean affiliation of the device is not in doubt. The first image shown while the device starts up is the Arch of Triumph in Pyongyang, and upon booting a Moranbong Band concert loops on the TV while the device waits for a song to be chosen. Dissonance begins to set in upon exploring the rest of the software.
The V700 could be at home in a Chinese KTV room, with software that is fully “online” — recordings of performed songs can be uploaded to the vendor’s cloud, new songs (all Chinese) can be downloaded to the machine, and WeChat integration allows modifying the queue from a smartphone.
It supports both Wifi and wired Ethernet to provide these features. A WeChat payment structure also allows a central controller to dole out timed sessions with the machine to paying customers.
How would any of this work in the offline world of Pyongyang?
The Karaoke content also doesn’t provide immediate answers to the origins of the device. Some videos feature the “Hana 하나” watermark, while others are labeled with the competing “Mokran 목란” brand. Many others are titled, generically, “7.27”.

The Mokran Video logo before one collection of songs (Photo: North Korea Tech)
While many of the flashy features make use of the internet, the device functions perfectly well offline, and with hundreds of pages of preloaded karaoke, would be of immediate value within Pyongyang, even without those features.
Under the plastic veneer
As a commercial device used in group settings, the V700 has a very different threat model from the personal devices that have become ubiquitous around Pyongyang in recent years.
Powered by an Allwinner ARM processor, the song data is on an easily swappable (one screw holds a flap in place to remove) full sized hard drive labeled “North Korean Songs” in Chinese.
If that was all there was to it though, you wouldn’t be reading this article.
While the Chinese songs on the hard drive can be played on any computer they are connected to, the 42 gigabytes of North Korean media is encrypted, and the files cannot be opened on other devices.
The device itself has a file manager and open USB ports. It allows customers to plug in their own USB sticks to sing songs off, and to save their recordings to. It also allows installation of other Android applications and copying of arbitrary user-accessible files to a USB stick, which makes access to the device very easy.
Most of the system software is a generic Chinese KTV system. The main question in my mind while investigating and figuring out how to decode the protected content was where the custody line was between Chinese and North Korean.
Had a North Korean client provided a package of content to be included with a stipulation that it should be protected, or had the software itself been customized by North Korean programmers like the smartphones and tablets in Pyongyang? Were there clues to the North Korean entity behind this device?
The full user experience of the karaoke device is implemented within a single monolithic Android application that itself references a host of system libraries for interacting with playing the karaoke through the external HDMI video connection.
Some of these libraries immediately caught my eye as “out of place” — an extremely small “libscmediafiledecrypt.so” reports a log message labeling itself “libktv” every time an encrypted file is accessed, and provides a way for files to be encrypted by the Android serial number of the device.
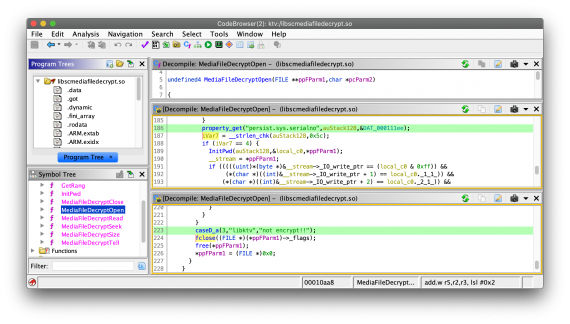
After further investigation it turns out this library is not actually performing any encryption or decryption. A second library, “libsclib.so” exports a function “ScEncrypt_getPicEncryptKey” as part of a separate file encryption system. This library, while also not performing file decryption of files at runtime, perhaps holds a clue of attribution, as the other uses of “sclib” and of the “PIC” identifier can be traced to the Pyongyang Informatics Center.
Deeper investigation of the DRM (digital rights management) present on the device yields that it is in fact a modified version of the Allwinner CedarX media framework that is performing the file decryption.
While the relevant “libcdx_stream” library is not open source, its source has been uploaded in the context of several other Chinese Android development source trees. The binary present on the v700 features a substantially different encryption method than is visible in the version provided by Allwinner.
The core library uses a fixed encryption key that would be compiled into the binary. The V700 consults both “/proc/cpuinfo” to learn the CPU serial number of the device it is on, and a binary file associated with the device file system structure as part of its method for determining its AES (Advanced Encryption Standard) key. It then ignores all of these device-specific items, and reverts back to a static key “87654321” stored in the binary.
The obfuscation and complexity involved is not found in a standard cedar release, and indicates coding work downstream from the allwinner distribution.

Common North Korean convention is to highlight the name of Kim Jong Un in media (Photo: North Korea Tech)
The goods
The 42 gigabytes of North Korean Karaoke packaged on the V700 have been made available in a decoded form at https://archive.org/details/tianchi-v700-ktv , and are being graciously hosted by the Internet Archive for archival purposes.
Some highlights from the collection include
https://archive.org/details/tianchi-v700-ktv-92136 – the canonical pangapsumnida song
https://archive.org/details/tianchi-v700-ktv-92010 – arirang
https://archive.org/details/tianchi-v700-ktv-940280 – the CNC song
https://archive.org/details/tianchi-v700-ktv-91599 – KCC logo appears on many songs
https://archive.org/details/tianchi-v700-ktv-940258 – tech progress
https://archive.org/details/tianchi-v700-ktv-92305 – tongil (unity), a woman driving through the tongil district and then visiting the unification monument on the southern highway
https://archive.org/details/tianchi-v700-ktv-92176 – summer water skiing
https://archive.org/details/tianchi-v700-ktv-960233 – kimchi song
https://archive.org/details/tianchi-v700-ktv-990001 – the one chinese song that was in the collection
https://archive.org/details/tianchi-v700-ktv-960071 – this VCD wasn’t properly split when it was put on the device – it actually is 10 or so songs in a row. (one of the higher quality sets as well)
The background Morangbong band concert is also there: https://archive.org/details/tianchi-v700-ktv-970013


