It’s been a busy few days for North Korea watchers. After a couple of weeks of no solid news on the Sony hack, the FBI has finally released a few details from its preliminary investigation
That’s great news because there has been a lot of confused reporting on the case. The leaks from the FBI have generally come through national security reporters, not computer security reporters, so we’ve seen a number of differing claims:
There was general confusion about the common hacker practice of routing traffic through compromised machines in other countries. Here are some headlines from last week:
- Evidence in Sony hack attack suggests possible involvement by Iran, China or Russia, intel source says – Fox News
- U.S. officials now believe Sony hack attack was launched inside North Korea & routed through servers in Taiwan – NBC News
- Sony cyberattack originated from five-star Bangkok hotel – Daily Mail
Some media outlets reported that portions of the malware code were in Korean while others said the malware was compiled on a computer that had its language environment set to Korean.
Not only is that an important difference, but it also doesn’t differentiate between the Korean language used in the South and that used in the North. There are subtle differences, just as there are in variations of English, and some operating systems take that into account.
So, it was good news when the FBI made its first public statement. The highlights, straight from the FBI news release:
- Technical analysis of the data deletion malware used in this attack revealed links to other malware that the FBI knows North Korean actors previously developed. For example, there were similarities in specific lines of code, encryption algorithms, data deletion methods, and compromised networks.
- The FBI also observed significant overlap between the infrastructure used in this attack and other malicious cyber activity the U.S. government has previously linked directly to North Korea. For example, the FBI discovered that several Internet protocol (IP) addresses associated with known North Korean infrastructure communicated with IP addresses that were hardcoded into the data deletion malware used in this attack.
- Separately, the tools used in the SPE attack have similarities to a cyber attack in March of last year against South Korean banks and media outlets, which was carried out by North Korea.
Those conclusions led the FBI to assert that “the FBI now has enough information to conclude that the North Korean government is responsible for these actions.”
That’s quite a claim.
Computer security experts will tell you that absolute attribution in cyber attacks is really difficult. Unless you happen to catch an attacker in the act, get their computer or have them admit it, the best you can usually do is strongly suspect someone.
That’s exactly what security companies have done in the past when it’s come to attacks blamed on North Korea.
Earlier this year, McAfee published a detailed report on what it called “Operation Troy,” which was a cyber espionage campaign against South Korea. The company was able to present compelling evidence that a string of cyber attacks were in fact linked and carried out by different parts of the same group.
It found, for example, that portions of source code used in each attack matched, that similar keywords and terms were found in different variants of the malware, that attacks used the same methods to avoid detection and, perhaps most convincing, that they all used the same password to compress stolen data.
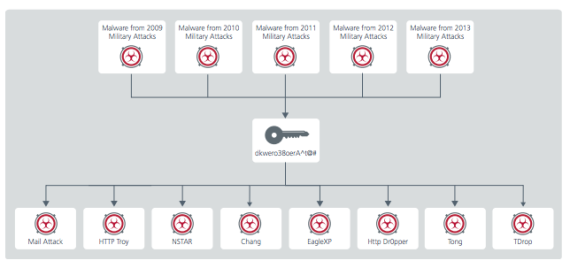
McAfee found a common password used to compress data in a string of cyber attacks. (Image: McAfee)
But McAfee stopped short of blaming anyone — precisely because it’s so difficult.
And Crowd Strike, which has also been looking at the attack and has closely followed the same hacker group, blogged about the FBI announcement but carefully avoided referring to the culprit of the Sony hack as North Korea.
So sure, North Korea might be the most obvious culprit — and many would say probably is responsible — but there’s still no conclusive evidence. It’s a bit like scientists trying to prove complex theories. Everything might point to one answer, but they’re hesitant to say so unless they can prove it without a doubt.
So, back to the FBI’s assertion on North Korea’s guilt.
Based on what’s been made public, there doesn’t appear to be enough to convict North Korea without a shadow of doubt. Of course, the FBI likely has a lot more information that it hasn’t made public, but we haven’t see that.
The waters are particularly muddy in this case because so much of the incident, from the emails to reporters to the leaking of data and taunting of investigators, is so different from previous attacks.
Assuming the FBI data is solid, it’s certainly an indicator of possible North Korean involvement, but we’re still a long way from understanding the entire incident.
Hopefully this week, some of the computer security companies that took a role in investigating the hack will begin speaking and offering their technical interpretation of the hack and how it operated.
I see several possibilities, the correct one of which we’ll likely never prove:
- The hack was carried out by North Korea
- The hack was carried out by a third-party on behalf of North Korea, with access to the country’s hacking infrastructure
- The hack was carried out by a third-party for other reasons and they latched onto the movie because it was in the headlines so much
With Sony saying they are now exploring release of the movie through video-on-demand services, the activities of the hackers might not be done. It should be an interesting few days ahead.